About Affiliates Cisco Systems, Inc. These attributes are retrieved at the time user authentication occurs using XAUTH, and are then combined with group attributes and applied during Mode-Configuration. EzVPN provides the following general functions in order to simplify the configuration process: EzVPN provides the following general functions in order to simplify the configuration process:. Example shows the configuration of the policy attributes locally on the EzVPN server on a per-group basis. 
| Uploader: | Zukora |
| Date Added: | 14 October 2013 |
| File Size: | 12.41 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 74089 |
| Price: | Free* [*Free Regsitration Required] |
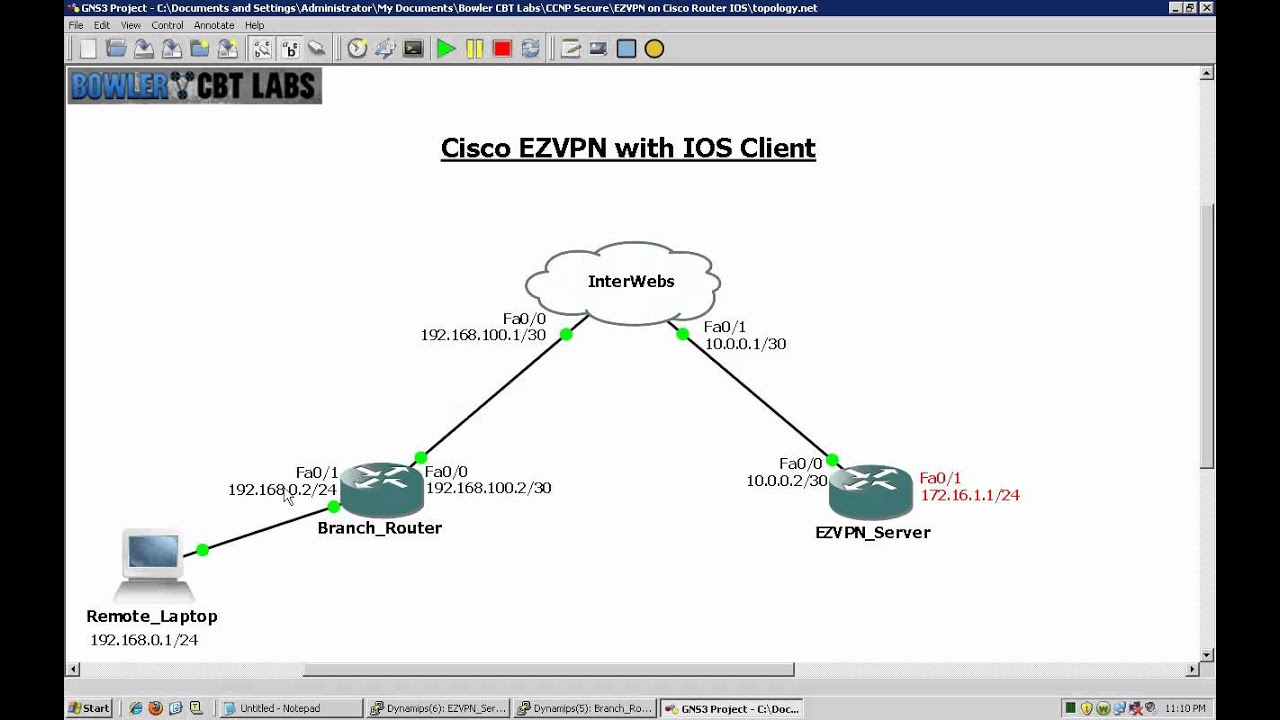
Chapter Description This chapter covers IPSec features and mechanisms that are primarily targeted at the authentication of remote access users. A user attribute overrides a group attribute value. The attributes may also be applied on ezvph per-user basis. These attributes are retrieved at the time user authentication occurs using XAUTH, and are then combined with group attributes and applied during Mode-Configuration.
An alternate mechanism to provide EzVPN server redundancy is to push the backup server's address list down to the client as an attribute. See All Related Articles. Example shows how to monitor an EzVPN client configuration. Sample Chapter is provided courtesy of Cisco Press. The dzvpn to be pushed can be defined locally on the EzVPN server or defined on a AAA server and defined either on a per-group or per-user basis.
Cisco ASA EZVPN (Revisited)
This mode allows the EzVPN client to present a full, routable network to the tunneled network. EzVPN provides the following general functions in order to simplify the configuration process:.
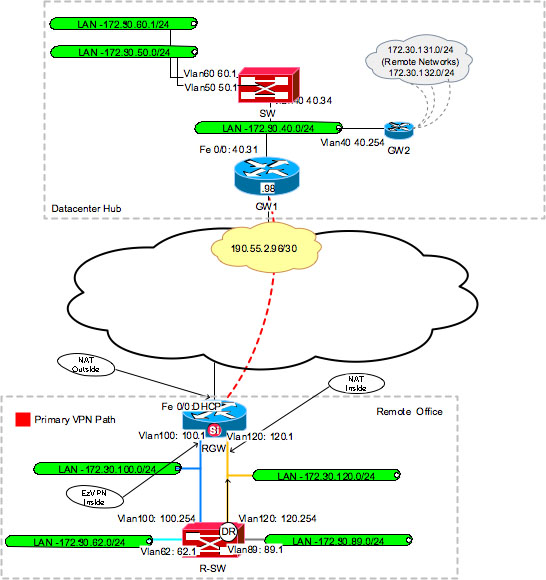
Home Shop By Cert New! This is a requirement of the Cisco AAA implementation. Example shows the policies configured on a AAA server on a group basis. The client keeps track of the mappings so that it can be forwarded to the correct host on the private network.
A couple of very useful attributes for telecommuter scenarios ezv;n max-logins and include-local-lan. About Affiliates Cisco Systems, Inc. Minimal configuration is required at the EzVPN client.
Example shows the client configuration with multiple EzVPN server peer addresses manually configured on the client.
Cisco ASA EZVPN (Revisited) | PeteNetLive
In this mode, all traffic from the client side uses a single IP address for all hosts on the private network. The include-local-lan attribute is very useful in scenarios in which the telecommuter's LAN has resources, such as printers, attached to the LAN and access to these resources is required when the VPN tunnel is up. In a large corporate environment with hundreds of sites, managing the IPSec configuration can get quite tedious.
Without the access list, only traffic to and from the "inside" subnet 1. The client configuration determines which mode is being used. Therefore, notice the use of the string cisco as the vpngroup password. The ACL permits networks behind the "inside" network As you saw in Chapter 2, "IPSec Overview," for an IPSec tunnel to be established between two peers, there is a significant amount of configuration required on both peers.
Negotiating tunnel parameters— This is done with encryption algorithms, SA lifetimes, and so on. Example shows the configuration of the policy attributes locally on the EzVPN server on a per-group basis. The max-logins attribute allows the administrator to restrict the number of simultaneous IPSec connections from the same user to the gateway. Note the ACL under the mode network-extension in the configuration.
Dead peer detection is on by default on the EzVPN clients. The tunnel on the EzVPN client can be initiated automatically or manually, or it could be traffic triggered, depending on the configuration or type of EzVPN client clidnt. EzVPN provides the following general functions in order to simplify the configuration process: Redundancy is always an integral part of any IPSec design and, in the case of EzVPN dead peer detection along with backup peer list, makes such a design possible.

No comments:
Post a Comment